Ericsson ECM (Enterprise Content Management) solution Vulnerable to CSV Injection (CVE-2021-41390)
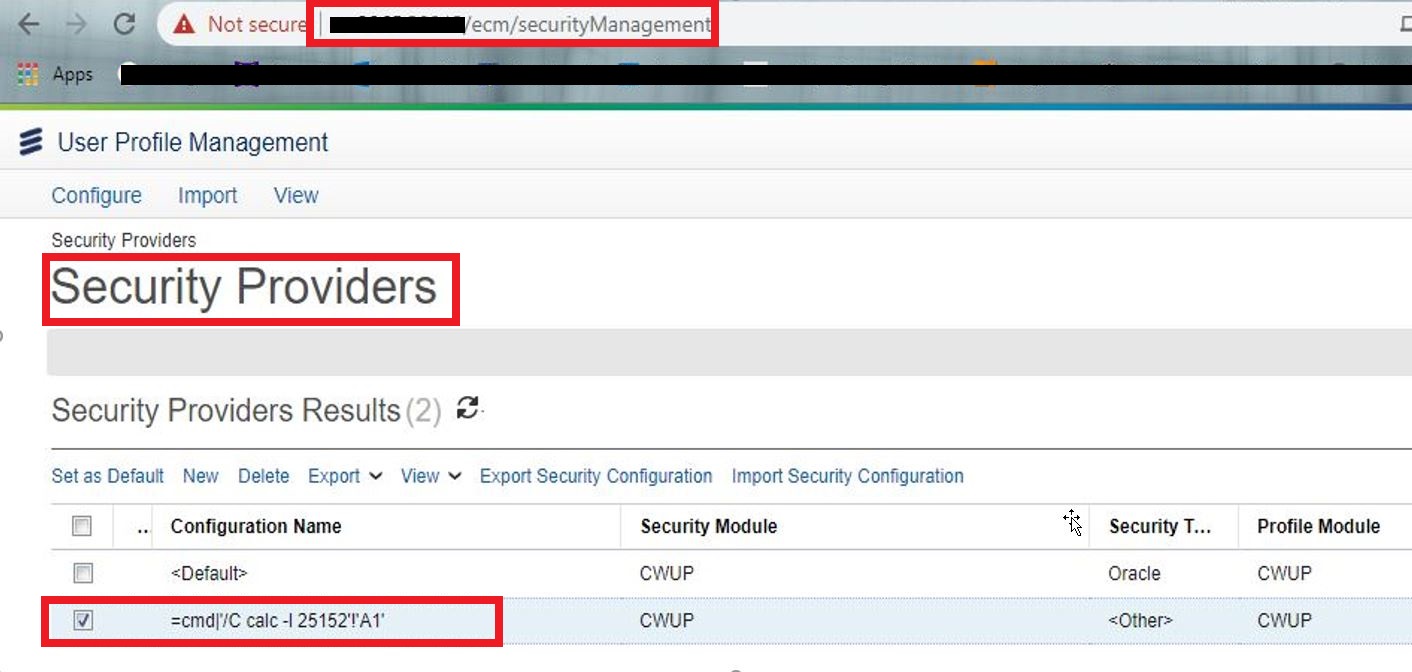
Dear Reader, I was able to identify CSV Injection in Ericsson ECM (Enterprise Content Management) solution Version: 18.0 (0331) R1E CVE ID: CVE-2021-41390 Below are its details: # Software description: Ericsson Catalog Manager allows customers to rapidly launch and enable new innovative offerings with simple user experience and enterprise product, service & resource catalog capabilities. # Technical Details & Impact: It was observed that Security Provider Endpoint in User Profile Management Section is vulnerable to CSV Injection , using CSV injection; Maliciously crafted formulas can be used for three key attacks: Hijacking the user's computer by exploiting vulnerabilities in the spreadsheet software, such as CVE-2014-3524. Hijacking the user's computer by exploiting the user's tendency to ignore security warnings in spreadsheets that they downloaded from their own website. Exfiltrating contents from the spreadsheet, or other open spreadsheets. # POC Lo...