Microsoft Teams Webinar Vulnerable to CSV Injection Vulnerability
Dear reader,
While testing different features of TEAMS, I find out a CSV injection vulnerability in TEAMS Webinar feature, where any external user, or attacker can register himself for attending public webinar and in webinar registration page he can inject a malicious payload which will executed once the admin download the attendees list.
As per Microsoft they are not accepting it as high/medium security bug (which I totally Disagree) and not eligible for bounty or hall of fame, also they provided the permission to disclose this publicly.
As per Microsoft the admin has to click enable button once he open the report. For which I mentioned them multiple times that admin will always trust the report as its coming from Trusted source which in this case is Microsoft and 95% of times he will click on Enable button and payload will be executed.
Anyways lets start with the Vulnerability details, At the end of this document I will give a bonus trick on how to find publicly available webinars which can be exploited using this vulnerability.
=======================Vulnerability Details=======================
Admin Side
To create and test the vulnerability locally, please follow below admin steps:
1. Initiate the webinar from Microsoft Teams.
2. Click on Custom registration Form.
3. Create Custom questions in the form or select the organization Field in the Form
4. Submit the Form.Attacker Side
Below are the Steps to exploit the CSV injection.
1. Open the newly created registration Form in browser
2. Fill in your name email
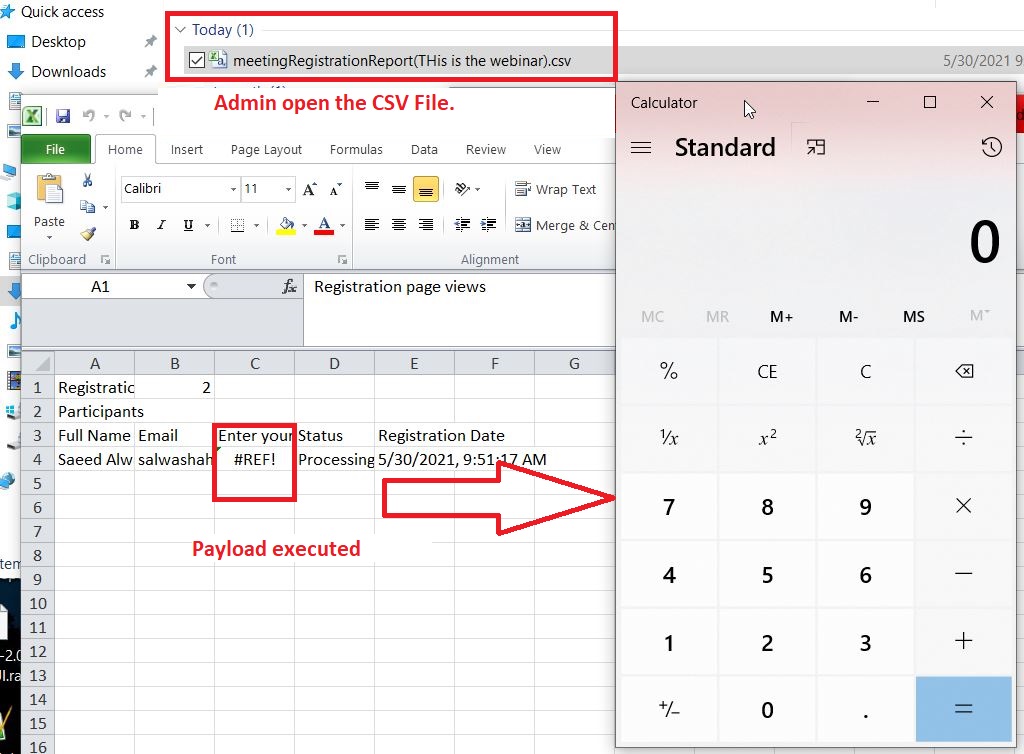
3. In Organization or any custom question, input your csv injection payload. For test case I just put a test payload which will open the Calculator on admin system
4. Click on register button. Now your payload is submitted to the admin
Once the webinar ends, admin download and open the attendee list from TEAMS the CSV file will ask for ENABLED / Disable, As most of the time the webinar admins are non technical they will click on enable button as they trust the source of downloaded file. This will lead to payload execution.








Comments
Post a Comment