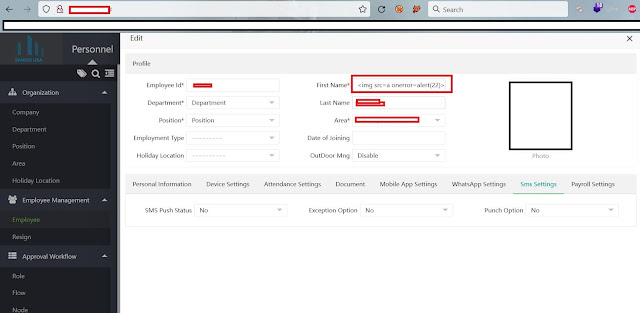
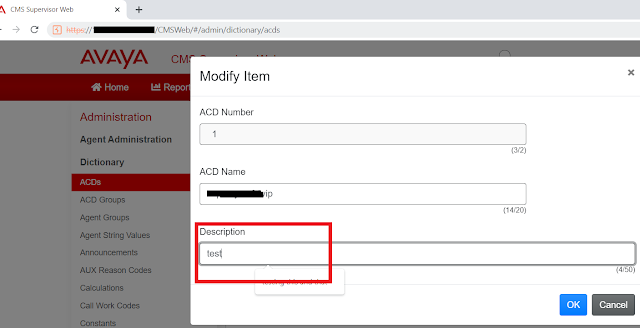
Bypassing BurpSuite "Failed to connect to website:port" issue

Hi readers, When performing penetration testing, it’s common to run into situations where an application or web portal works perfectly in a browser, but refuses to load once you route traffic through your interception proxy(e.g. Burp suite). Instead of the expected traffic flow, you might be greeted with errors such as: Error Failed to Connect to <website:port> This happens because some applications and servers enforce stricter connection requirements, such as enforcing TLS versions, specific cipher suites, or HTTP/2 negotiation. which the proxy cannot always handle correctly on its own. The Solution: Proxy Chaining (Upstream Proxy): The workaround is to introduce an additional proxy layer that sits between your BurpSuite and the destination server . Your interception proxy connects to this new proxy, which then handles the final connection to the target. This approach is commonly called proxy chaining or upstream proxying . It ensures that your interception tool can still ...